It could be fun and effective to show simple but interesting hacking demo while discussing application security with clients, to show how easy it is, and how serious the results could be.
One of the recommended "simple demo" is Web Parameter Tampering, on payment gateway.
Scenario:
- When people are going to pay for an item online, it is not difficult to change the price (so-called "Web Parameter") with the assistance of hacking tools.
- There are easy tools for Web Parameter Tampering. I take TamperIE as an example.
Tool: TemperIE (Download: http://www.bayden.com/tamperie/)
Demo Site for a "successful" tempering:
I would suggest you go through with above demo site first.
Here I "test" this with an online shop......Let's see if I could succeed.
Important Note: I do not engage hacking as a habit, but to share with the public how back guy would perform hacking. Through this exercise, good guy understands how bad guys act, and try a different way to make the bad guy a hard time.
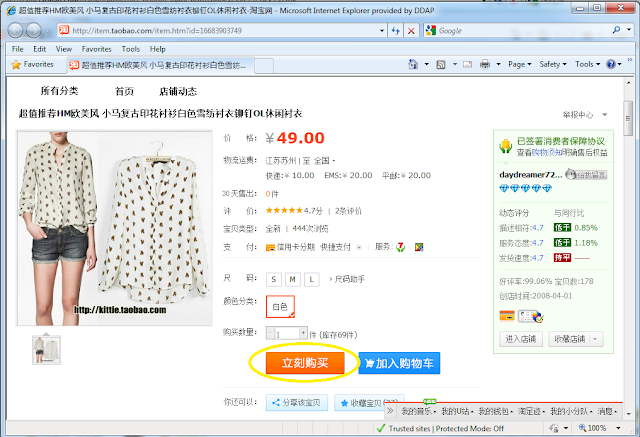
#1 - I (a bad guy) would like to purchase a blouse online, however, I think $45 is too expensive for me.
#2 Once I click "pay now", my pre-installed parameter tampering tool prompts, and shows me parameters on this webpage. Price is one of those as highlighted.
#3 $49 +$30 shipping. Total $79. Too expensive for me! So I change the price to $9 with the tool.
#4 However......The website is smart enough to detect the change of a parameter (the price).
#5 How Taobao detect this? We could see a parameter "SecStrNoCCode", which is believed to be a hash of the page and is used to check against the change of web parameters from page to page. Any change of parameter would induce a different hash. My best guess of the full meaning of this name is "Security String No Change of Code"




沒有留言:
張貼留言